Introduction about Pum.bad.proxy
Pum.bad.proxy is classified as a destructive Trojan virus
which can damage targeted computer severely. As usual, if you have performed
some dangerous internet activities like downloading infectious free softwares
and visiting hacked websites, you probably will get your computer infected by
Pum.bad.proxy. So you really should be more careful about your internet
activities. Once your computer is compromised, it’s not an easy thing to remove
Pum.bad.proxy from your computer completely.
Pum.bad.proxy can set itself as a start up process without asking your
permission as soon as it breaks in your computer successfully. So it can be
activated to perform its malicious activities immediately when you open your
computer. Pum.bad.proxy is able to create not only its own registry but also
security loopholes to invite many malicious things such as browser hijacker,
adware, ransomware and so on from your computer. Therefore, your limited system
resource will be consumed largely by these junk files and this Trojan virus so
that your computer running speed will become incredibly slow because there is
no enough room for normal processes to run. The worst thing of keeping
Pum.bad.proxy in your computer is that it allows hackers get inside your
computer. It helps them to connect your computer remotely so that they can take
control of your computer in order to steal your confidential information like
credit card account and password for making illegal money. Under such
circumstance, you are highly recommended to take proper method to remove
Pum.bad.proxy from your computer in time before it causes more unimaginable
damages on your computer.
1. It runs itself automatically when you launch windows.
2. It drops many malicious files to mess up the system.
3. It takes up high CPU usage to degrade the PC performance.
4. It opens backdoor for inviting more bad stuffs in your computer.
5. It allows the hackers to connect your computer to steal your privacy.
6. It is able to block the firewall and antivirus programs.
Recommanded Solution:
Certain computer expertise is required to perform the manual removal. If you are not comfortable with taking the risk of deleting virus files, please use this powerful Automatic Virus Removal Tool to help you get things done perfectly.
How to Remove Pum.bad.proxy
Before the removal, please first back up your system! You should be extremely careful when deleting any file, because any mistake may lead to system crashes and other severe consequence.
METHOD 1. Manual Removal
Step One:
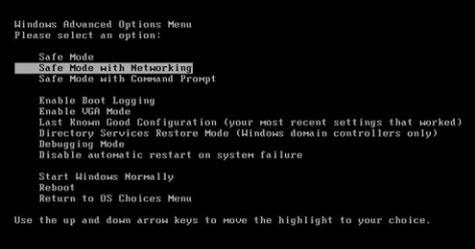
Reboot the computer and before Windows interface loads, hit F8 key repeatedly. Choose “Safe Mode with Networking” option, and then press Enter key. System will load files and then get to the desktop in needed option.
Step Two:
Open Windows Task Manager and end virus processes. There are three ways to launch the Task Manager
① Press keys Ctrl+Alt+Del.
② Press keys Ctrl+Shift+Esc.
③ Press the Start button→click on the Run option→Type in taskmgr→press OK.
Step Three:
Click “Start” button and open the “Control Panel”, then double-click “Folder Options”. When the Folder Options window shows up, please click on the “View” tab, tick “Show hidden files and folders” and unmark “Hide protected operating system files(Recommended)” and then press OK.
Step Four:
Step Three:
Click “Start” button and open the “Control Panel”, then double-click “Folder Options”. When the Folder Options window shows up, please click on the “View” tab, tick “Show hidden files and folders” and unmark “Hide protected operating system files(Recommended)” and then press OK.
Step Four:
Open Start menu and click on the “Search programs and files” box. Then delete Pum.bad.proxy files:
%AppData%\random.exe
%CommonAppData%\random.exe
C:\Windows\Temp\random.exe
%Temp%\random.exe
C:\Program Files\random
Step Five:
Open Registry Editor by pressing Windows+R keys, type in regedit and click “OK” to launch the Windows Registry. Then delete all Pum.bad.proxy registry entries and keys.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Wpm
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows
NT\CurrentVersion\Image File Execution Options\MpCmdRun.exe
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image
File Execution Options\MpUXSrv.exe
To completely delete Pum.bad.proxy, you need to know that the manual removal above may not be able to remove virus completely, because the creators of virus are always updating the virus version.Besides,any tiny mistake during the manual removal process may lead to severe consequences. Therefore,to ensure a complete and safe virus removal, it’s recommended that you get rid of virus with Automatic Pum.bad.proxy Removal Tool.
EASY & EFFECTIVE
1. Virus Scanner - powerful,
professional and easy-to-use
Auto Virus Removal Tool is a powerful,
professional and easy-to-use application that will safely and effectively scan
the computer’s memory, registry, cookies and files for infected items. A small
action will remove all infections, so it is especially simple for new users.
2. Spyware HelpDesk – Free customized fix
Spyware
HelpDesk is a unique and highly effective interface
through which you can contact our technical support department! If our tool is
unable to remove an infection from your computer, our team will be happy to
generate a customized fix for you, which is absolutely free.
3. System Guards - Protect your system
With integrated techniques, the
new feature System Guards protects your system through blocking malicious
processes from executing and running on the system. You can then gain the whole
control over all processes including those authorized and unauthorized ones.
4. Network Sentry - guarantee the Internet safety
Network Sentry is to guarantee your Internet
safety and security. It prevents malicious software from modifying networking
settings such as HOSTS files, Windows system files, DNS servers and explorer
homepage settings. You don’t need to worry about encountering unauthorized
redirections as this tool will notify you if any changes are made.





No comments:
Post a Comment